What Is VPN (Virtual Private Network)
What Is VPN (Virtual Private Network)?
✍: FYIcenter.com
![]() VPN (Virtual Private Network) refers to a virtual network whose traffic
is encapsulated and transmitted over a public network.
VPN (Virtual Private Network) refers to a virtual network whose traffic
is encapsulated and transmitted over a public network.
There are a number of protocols available for setting up VPNs.
1. IPsec (Internet Protocol Security) - IPsec authenticates and encrypts the packets of data to provide secure encrypted communication between two computers over an Internet Protocol network. It is used in virtual private networks (VPNs).
As a part of the IPv4 enhancement, IPsec is a layer 3 OSI model or internet layer end-to-end security scheme. In contrast, while some other Internet security systems in widespread use operate above layer 3, such as Transport Layer Security (TLS) that operates at the Transport Layer and Secure Shell (SSH) that operates at the Application layer, IPsec can automatically secure applications at the IP layer.
IPsec was initially specified by RFC 1825 through RFC 1827 in 1995.
2. IKE (Internet Key Exchange) - IKE is part of the IPsec protocol suite for setting up a security association. It uses X.509 certificates for authentication ‒ either pre-shared or distributed using DNS (preferably with DNSSEC) ‒ and a Diffie–Hellman key exchange to set up a shared session secret from which cryptographic keys are derived.
IKE was initially specified by RFC 2409 in 1998.
3. PPTP (Point-to-Point Tunneling Protocol) - In PPTP, the Point-to-Point Protocol (PPP) is wrapped inside the TCP/IP protocol, which provides the Internet connection.
PPTP was developed in 1999 by a vendor consortium formed by Microsoft, Ascend Communications (today part of Nokia), 3Com, and other groups.
PPTP, specified in RFC 2637, operates at Layer 2 of the OSI model. It uses TCP port 1723 and IP port 47 and supports two types of information flow:
- Control messages for managing and eventually tearing down the VPN connection. Control messages pass directly between VPN client and server.
- Data packets that pass through the tunnel, i.e. to or from the VPN client.
4. L2TP (Layer 2 Tunneling Protocol) - uses encryption ('hiding') only for its own control messages (using an optional pre-shared secret), and does not provide any encryption or confidentiality of content by itself. Rather, it provides a tunnel for Layer 2 (which may be encrypted), and the tunnel itself may be passed over a Layer 3 encryption protocol such as IPSec.
L2TP was published in 2000 as proposed standard RFC 2661. The entire L2TP packet, including payload and L2TP header, is sent within a User Datagram Protocol (UDP) datagram. A virtue of transmission over UDP (rather than TCP) is that it avoids the "TCP meltdown problem".
5. OpenVPN - OpenVPN allows peers to authenticate each other using pre-shared secret keys, certificates or username/password. When used in a multiclient-server configuration, it allows the server to release an authentication certificate for every client, using signatures and certificate authority.
OpenVPN was written by James Yonan and released in 2001 as a free software. Visit openvpn.net for more information.
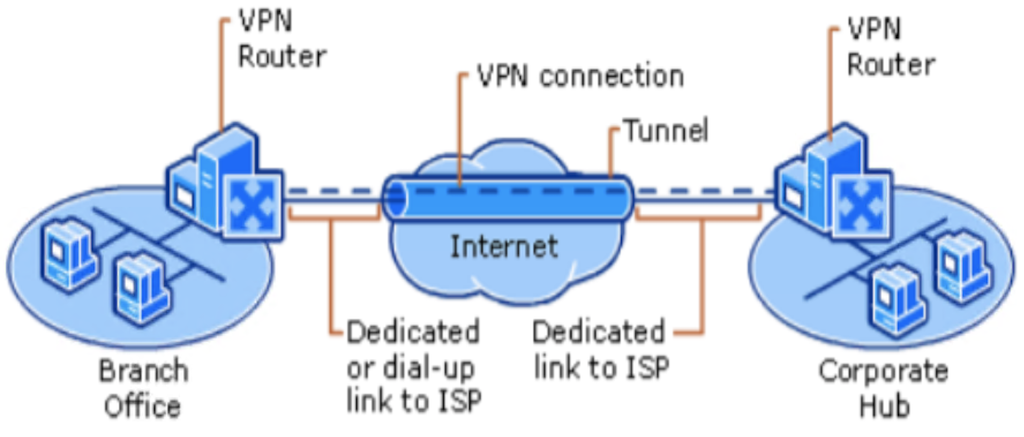
The picture illustrates the VPN (Virtual Private Network) architecture:
⇒ L2TP VPN Server on TP-Link Router
⇐ VPN (Virtual Private Network)
2022-05-01, 1743🔥, 0💬